Introduction: The Era of Data Protection Mandates
The management of personal data has evolved from a mere technical concern into a core legal and ethical imperative. In the modern digital economy, virtually every organization processes data that is subject to stringent rules and regulations enacted across various jurisdictions.
Data Protection Regulations Compliance is no longer optional; it is the bedrock of corporate trust and a fundamental prerequisite for global business operations. Failure to comply with key mandates, such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and countless others, can result in crippling fines, severe reputational damage, and loss of market access.
This definitive guide provides Chief Compliance Officers (CCOs), Legal Counsel, and IT Security professionals with a structured, in-depth framework for navigating the complex web of global data protection regulations. We will break down the essential principles, key regulations, and strategic steps necessary to build a robust, scalable, and compliant data governance program, maximizing search engine visibility and targeting high-value compliance-related AdSense revenue.
Foundational Principles of Modern Data Protection
Despite the geographic diversity of regulations, nearly all modern data protection laws are built upon a common set of core principles that govern the lawful processing of personal data.
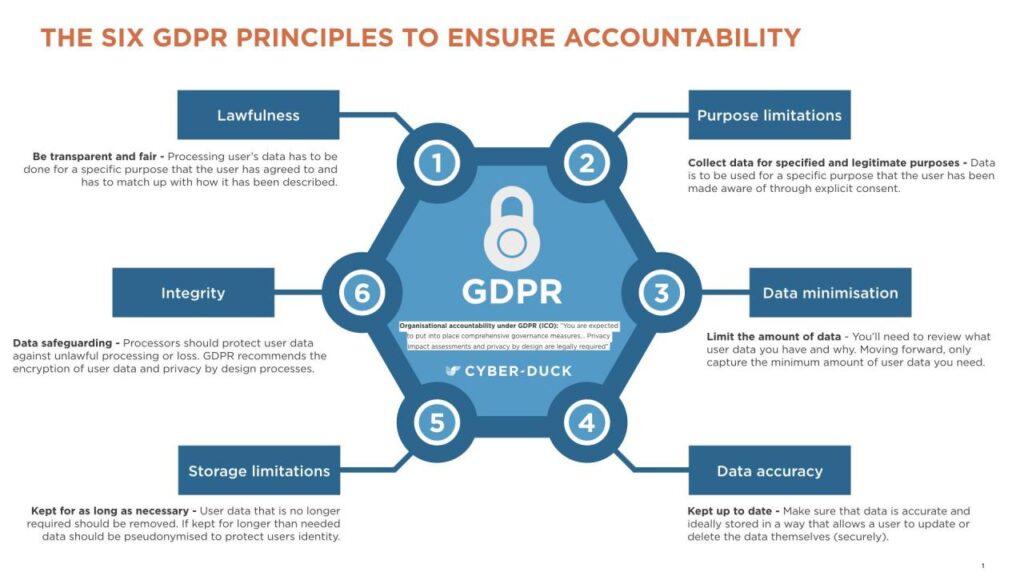
A. Lawfulness, Fairness, and Transparency
This principle mandates that data must be processed lawfully, fairly, and in a transparent manner in relation to the data subject.
Lawfulness: Processing must have a defined legal basis (e.g., consent, contractual necessity, legal obligation, vital interests, public task, or legitimate interests). Explicitly documenting the legal basis for every data process is essential.
Fairness: Data processing should align with the reasonable expectations of the individual concerned. Covert or deceptive data practices violate this principle.
Transparency: Organizations must provide clear, concise, and accessible information to data subjects about who is processing their data, why, and how long it will be retained. This is typically achieved through comprehensive privacy policies and notices.
B. Purpose Limitation
Personal data must be collected for specified, explicit, and legitimate purposes and not further processed in a manner that is incompatible with those purposes.
Specificity: Organizations must clearly define the exact reason for data collection before starting the process. Vague statements like “for business improvement” are typically insufficient.
Compatibility: If data is to be processed for a new purpose later, that purpose must be assessed for compatibility with the original purpose. If incompatible, a new legal basis must be established, often requiring fresh consent.
C. Data Minimization and Accuracy
The core concept here is only collecting and retaining what is absolutely necessary and ensuring its quality.
Minimization: Data collected should be adequate, relevant, and limited to what is necessary in relation to the purposes for which they are processed. This often means auditing forms and processes to eliminate unnecessary data fields.
Accuracy: Data must be accurate and, where necessary, kept up to date. Organizations must implement reasonable steps to ensure inaccurate personal data is rectified or erased without delay.
D. Storage Limitation
Personal data must be kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed.
Retention Schedules: Implementing detailed data retention policies and schedules is crucial. This mandates the systematic, secure deletion or anonymization of data once its business necessity and legal retention period expire.
Deletion Protocols: Organizations must have defensible and verifiable protocols for permanently deleting or anonymizing data across all systems, including backups and archives.
E. Integrity and Confidentiality (Security)
This principle requires personal data to be processed in a manner that ensures appropriate security of the personal data, including protection against unauthorized or unlawful processing and against accidental loss, destruction, or damage, using appropriate technical or organizational measures.
Technical Measures: Utilizing tools such as encryption, pseudonymization, network firewalls, and strong access controls (IAM).
Organizational Measures: Implementing training programs, internal policies, access control segregation, and data protection impact assessments (DPIAs).
F. Accountability
The most modern principle, which places the onus on the data controller to demonstrate compliance with all the above principles.
Documentation: Maintaining detailed records of processing activities, privacy notices, data sharing agreements, consent logs, security measures, and DPIAs.
Designated Roles: Appointing specific personnel, such as a Data Protection Officer (DPO) where legally required, to oversee compliance efforts.
 Key Global Regulations and Their Unique Demands
Key Global Regulations and Their Unique Demands
While the principles are similar, the specific application, scope, and penalties vary significantly across different major regulations.
A. General Data Protection Regulation (GDPR) (Europe)
The benchmark for global data protection, applying to any organization processing the personal data of EU residents, regardless of the organization’s location (extraterritorial scope).
Individual Rights (Data Subject Rights – DSRs): GDPR formalizes rights that organizations must facilitate, including:
Right to Be Informed: Detailed in privacy notices.
Right of Access: Access to all personal data held about them.
Right to Rectification: Correcting inaccurate data.
Right to Erasure (Right to Be Forgotten): Obligation to delete data upon request, under certain conditions.
Right to Restrict Processing: Halting data processing activities.
Right to Data Portability: Receiving their data in a structured, common, and machine-readable format.
Right to Object: Objecting to processing based on legitimate interests or for direct marketing.
Rights Related to Automated Decision Making and Profiling: Limiting decisions made solely by automated means.
Data Protection Impact Assessments (DPIAs): Mandatory for processing that is likely to result in a high risk to individuals’ rights and freedoms.
Breach Notification: Mandatory notification of a data breach to the supervisory authority within 72 hours of becoming aware, and to affected data subjects without undue delay if the risk is high.
B. California Consumer Privacy Act (CCPA) and CPRA (United States)
A landmark regulation in the U.S. that grants extensive rights to California consumers, enforced by the California Privacy Protection Agency (CPPA).
Expanded Definition of Personal Information: Includes household data and inferences drawn from data to create a profile, making the scope very broad.
Right to Opt-Out of Sale/Sharing: Consumers have the explicit right to direct a business not to sell or share their personal information. Organizations must post a clear “Do Not Sell or Share My Personal Information” link.
Right to Limit Use of Sensitive Personal Information (SPI): Consumers can limit the use or disclosure of sensitive data (e.g., precise geolocation, health data).
C. Lei Geral de Proteção de Dados Pessoais (LGPD) (Brazil)
Brazil’s comprehensive privacy law, modeled heavily on the GDPR, impacting any entity processing data of individuals located in Brazil.
Legal Bases: Requires one of the ten legal bases for processing, similar to GDPR, including the requirement for specific and informed consent.
Data Protection Officer (DPO): Requires the appointment of a DPO and mandates the creation of detailed Records of Processing Activities (ROPA).
D. Personal Information Protection Law (PIPL) (China)
China’s stringent, comprehensive data protection law, effective since late 2021, imposing significant restrictions on international data transfers.
Consent Requirements: Requires separate, explicit consent for processing sensitive personal information and for transferring personal information outside of China.
Cross-Border Data Transfer: Requires passing a security assessment, certification, or executing Standard Contractual Clauses (SCCs) before transferring data abroad, making this a complex operational hurdle.
Implementing a Unified Global Compliance Framework
To manage this complex regulatory environment, organizations must adopt a unified, risk-based approach rather than treating each regulation in isolation.
A. Data Mapping and Inventory
The foundational step is understanding what data you have, where it is, and who has access to it.
A. Identify Data Categories: Classify data into categories (e.g., customer, employee, sensitive, operational).
B. Locate Data Sources: Identify all systems, applications, and databases that collect, process, or store personal data.
C. Document Data Flows (Data Mapping): Track how data moves from initial collection to storage, processing, and ultimate deletion, including all third-party recipients.
D. Define Legal Basis and Purpose: For each processing activity identified, clearly document the specific legal basis (e.g., consent, contract) and the defined purpose.
B. Establishing Data Subject Rights (DSR) Management
Building a scalable process to handle DSR requests is critical for compliance with all major regulations.
A. Centralized Intake Portal: Create a single, accessible method (e.g., a web form) for individuals globally to submit requests (access, deletion, opt-out).
B. Verification Protocol: Implement robust identity verification procedures to confirm the requester is the data subject or their authorized agent, minimizing the risk of unauthorized disclosure.
C. Fulfillment Workflow: Automate the workflow to track the request, notify relevant departments (IT, Marketing, HR), conduct the necessary data retrieval/deletion/restriction actions, and document the completion within the mandated timeframe (e.g., 30 days under GDPR/CCPA).
D. Right to Opt-Out Enforcement: Implement “Do Not Sell/Share” flags that are seamlessly communicated across all internal systems and third-party advertising partners, particularly vital for CCPA/CPRA adherence.
C. Third-Party Risk Management (TPRM)
When data is shared with vendors, the organization remains accountable.
A. Vetting and Due Diligence: Require all third-party vendors (data processors) to provide evidence of their security controls, compliance certifications (e.g., ISO 27001), and a clear data protection policy.
B. Data Processing Agreements (DPAs): Mandate the signing of DPAs, which legally define the obligations of the processor, including security standards, breach notification procedures, and sub-processor approvals.
C. International Data Transfer Mechanisms: For cross-border data flows (e.g., EU to US), ensure the appropriate mechanism is in place, such as EU Standard Contractual Clauses (SCCs), or relevant certification frameworks (e.g., the new EU-U.S. Data Privacy Framework).
 Security Controls and Privacy by Design
Security Controls and Privacy by Design
Compliance is inextricably linked to information security. Privacy should be proactively embedded into system design.
A. Data Protection by Design and Default
This principle requires that data protection measures are considered and implemented from the very start of any project or system design, and that, by default, the strictest privacy settings are applied.
A. Pseudonymization and Anonymization: Implement these techniques to render data less identifiable, especially in development, testing, and analytics environments. Pseudonymized data remains regulated, while effectively anonymized data may fall outside the scope of many regulations.
B. Access Control Review: Strictly limit access to sensitive personal data (SPI) only to employees who require it for their direct job functions (Principle of Least Privilege).
C. Training and Awareness: Conduct mandatory, regular data protection training for all employees, tailored to their roles and level of access to personal data.
B. Breach Preparedness and Incident Response
Compliance requires not just preventing breaches, but having a clear, rapid plan for responding when they occur.
A. Detection Capabilities: Invest in Security Information and Event Management (SIEM) systems and threat detection tools that can identify unauthorized access or data exfiltration attempts quickly.
B. Communication Plan: Establish pre-approved communication templates and notification lists for engaging with regulatory authorities, legal counsel, and affected data subjects, ensuring timely notification is met (e.g., the 72-hour window under GDPR).
C. Post-Incident Review: Conduct a thorough review after every incident or near-miss to identify systemic failures and update the compliance framework and security controls accordingly.
Conclusion
Achieving compliance with global data protection regulations is not a one-time project; it is a continuous journey that requires sustained investment in technology, policy, and human capital. By adopting the principles of Lawfulness and Transparency, mastering the demands of GDPR, CCPA, and PIPL, and implementing a rigorous framework of Data Mapping and DSR Management, organizations can transform regulatory pressure into a competitive advantage. A strong, transparent commitment to data protection fosters consumer trust, opens doors to global markets, and solidifies the corporate reputation—all vital elements for maximizing long-term shareholder value and securing a reliable, high-quality stream of ad revenue.

 Key Global Regulations and Their Unique Demands
Key Global Regulations and Their Unique Demands Security Controls and Privacy by Design
Security Controls and Privacy by Design




